Web developers/ Students don't save your plain password in the database. There is a chance for HACKING!
Last week, I had checked a couple of companies website's source codes to shield them from hacking. It has been seen that, they are using plain password (as shown in the screenshot below) in their database. That is you can see the password of all registered users in the database using any database tool like PHPMYADMIN, SQLYOG etc. It can be noted that many users, using the same username and password for logging into multiple websites like gmail, onlinesbi etc. Thus hackers can easily enter into multiple website using your username and password which was stolen from a less secured website. So I recommend all of my readers to use different usernames and passwords in different websites.Now we can come to our topic. From time to time, servers and databases are stolen or compromised by hackers all over the world. With this in mind, it is important to ensure that some important user data, such as passwords, cannot be recovered. In this tutorial , I will explain how hash technique helps us to escape from these situations.
What is "hashing"
Before the brief discussion we want to know that what is hashing technique. The theoretical definition of hashing is given below.
Hashing converts a piece of data (either small or large), into a relatively short piece of data such as a string or an integer.Normally, all famous hashing algorithms are "one-way" algorithms means, it will convert your information (say password) into a string with some alphanumeric characters. md5(), crc32() etc are widely using hashing functions.
Hashing using PHP, An example!
In PHP, there are many built in functions for hashing and its format is very simple compared to other programming languages.An example PHP hash function is md5(). Please use this code for md5 hashing
From the screenshot, it is clear that the md5 function will convert the information into 32 character hexadecimal number (Number 0,1,2,3,4,5,6,7,8,9 and characters A,B,C,D,E,F). One hexadecimal character can be represented using 4 bits (ie 1=0001, and A=1010) thus md5 result set dimension is 128 bit.
You cannot reconstruct the original information (pravysoft calicut) from the result (00d79e8e609cfbdf5b75d80fdef96fb4).
[Note: Actually there are some hacking strategies to break/interpret md5, but that is out of scope of this tutorial, Ofcourse you can send me a request to know that techniques!!].
User Registration and Login Steps
Now we can check the user registration steps
1. User fills their information in the registration form
2. It is better to use password fields type as password (<input type="password" >)
3. Submitted data is received by the web-server
4. Convert submitted password to md5 code. Discard original password, it will not use anywhere!
5. Save this md5 data in the corresponding field in the database
Now we can check the steps for user login process
1. The registered user now type username and password in the login window.
2. The submitted password is converted to md5 code using md5 function.
3. The code will compare the usernames as well as md5 code based passwords.
5. If they match, it will grant access to the user.
Thus if any hacker stolen the database they will only get Md5 version of the password only. Not their original secret password!!. Thus the users are protected from password hijackers.
But there are also some chances for hacking the password encrypted using hashing algorithm. For showing a demo I am using another hashing function crc32() [md5 code width is 128 character, so for simulation it will take some time, the crc32() use only 32bits for decryption thus its simulation will complete faster]
<?php |
The screenshot below shows the result of the above code.
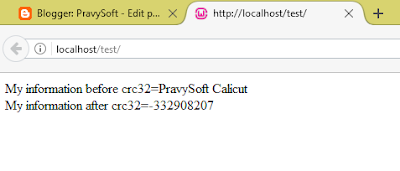
From the screenshot it is clear that, the hash code of the string "PravySoft Calicut" is -332908207. Ofcourse a hacker who has stolen the database cannot recover the string ( "PravySoft Calicut" ) from this number (-332908207). But he can login to the website using another password and that hack is explained below. As you know that cr32 using 32 bit encoding, thus it has only 2 to the power 32 (2^32) combinations only. Thus there is a chance for another string to produce the same hash code i.e -332908207. So if you know any other string which has the same hash code (say a duplicate) can be used to login to the website. Use following code for finding duplicate string
<?php |
It will take some time to get the duplicate key/string , after getting the duplicate key you can check the hash code of that duplicate key and hash code of your string are equal. (i.e It is same as that of the hash code of the example string "PravySoft Calicut"). Thus you can access to the website using this duplicate key without knowing original string.
How you can escape from this type of hacking. Better idea is to don't use low-range hashing algorithm like crc32. It is better to use Md5() or sha1() algorithms, They have 128 bit and 160 bit hash codes respectively, Thus finding a duplicate key is very difficult and it will take very long time to get duplicate key.
Some hacking sites are keeping large number of duplicate keys to decode the hash code (Hash code database size is in the range of petabyte, ie 1000 terabyte= 1 peta byte). So hackers can find duplicate keys of some hashcodes very easily [ I am not discussing the websites they store this data(I believes that it is unethical )]. It is also a major problem for web developers to protect their website from unauthorized access. So in the next section we will discuss, how you can block duplicate key access to your websites.
It is the time for a small tea!!, I will explain some-other security issues and ways and means to protect your site from hacking, see you soon in the next post!!